Add dedicated AWS IAM user to deploy
Table of Contents
The flow of adding a new user and enabling the required permissions is described below:
- Navigate to the Identity and Access Management (IAM) console of your AWS account and press the “Add users” button.
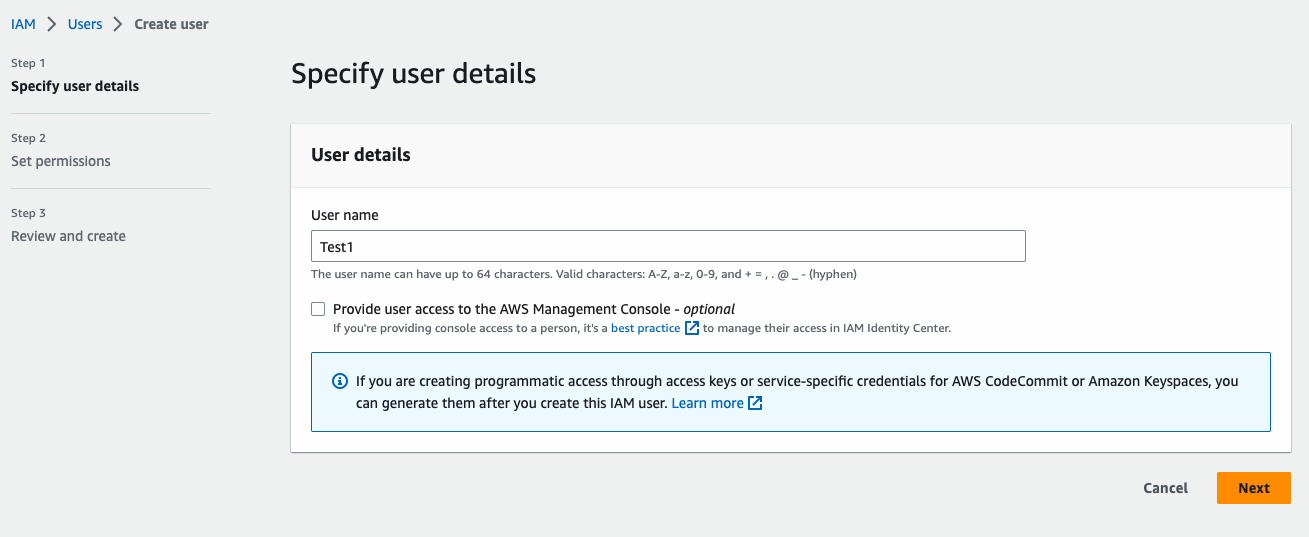
Figure 1: Add users
-
Add a user’s name and select password as AWS credential type.
-
Press the “Next: Permissions” button. A newly opened page will allow you to set permissions. Select “Create Policy”, switch to
JSONand paste the following policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"cloudformation:TagResource",
"cloudformation:UntagResource",
"cloudformation:CancelUpdateStack",
"cloudformation:CreateStack",
"cloudformation:DeleteStack",
"cloudformation:DescribeStacks",
"cloudformation:ListStacks",
"cloudformation:UpdateStack",
"cloudformation:GetStackPolicy",
"cloudformation:SetStackPolicy",
"cloudformation:ContinueUpdateRollback",
"cloudformation:RollbackStack",
"cloudformation:UpdateTerminationProtection",
"cloudformation:DescribeStackDriftDetectionStatus",
"cloudformation:DescribeStackEvents",
"cloudformation:DescribeStackResource",
"cloudformation:DescribeStackResourceDrifts",
"cloudformation:DescribeStackResources",
"cloudformation:DetectStackDrift",
"cloudformation:DetectStackResourceDrift",
"cloudformation:ListStackResources",
"cloudformation:GetTemplate",
"cloudformation:GetTemplateSummary",
"cloudformation:CreateChangeSet",
"cloudformation:DeleteChangeSet",
"cloudformation:DescribeChangeSet",
"cloudformation:DescribeChangeSetHooks",
"cloudformation:ExecuteChangeSet",
"cloudformation:ListChangeSets",
"cloudformation:CreateStackSet",
"cloudformation:DeleteStackSet",
"cloudformation:DescribeStackSet",
"cloudformation:DetectStackSetDrift",
"cloudformation:ListStackSets",
"cloudformation:UpdateStackSet",
"cloudformation:DescribeStackSetOperation",
"cloudformation:ListStackSetOperationResults",
"cloudformation:ListStackSetOperations",
"cloudformation:StopStackSetOperation",
"cloudformation:ActivateOrganizationsAccess",
"cloudformation:DeactivateOrganizationsAccess",
"cloudformation:DescribeOrganizationsAccess",
"cloudformation:CreateStackInstances",
"cloudformation:DeleteStackInstances",
"cloudformation:DescribeStackInstance",
"cloudformation:ListStackInstanceResourceDrifts",
"cloudformation:ListStackInstances",
"cloudformation:UpdateStackInstances",
"dynamodb:TagResource",
"dynamodb:UntagResource",
"dynamodb:ListTagsOfResource",
"dynamodb:CreateTable",
"dynamodb:DeleteTable",
"dynamodb:DescribeTable",
"dynamodb:UpdateTable",
"dynamodb:DescribeTimeToLive",
"dynamodb:UpdateTimeToLive",
"dynamodb:DescribeContributorInsights",
"dynamodb:GetResourcePolicy",
"iam:ListInstanceProfileTags",
"iam:ListPolicyTags",
"iam:ListRoleTags",
"iam:TagInstanceProfile",
"iam:TagPolicy",
"iam:TagRole",
"iam:UntagInstanceProfile",
"iam:UntagPolicy",
"iam:UntagRole",
"iam:CreateInstanceProfile",
"iam:DeleteInstanceProfile",
"iam:GetInstanceProfile",
"iam:ListInstanceProfilesForRole",
"iam:AddRoleToInstanceProfile",
"iam:RemoveRoleFromInstanceProfile",
"iam:CreatePolicy",
"iam:DeletePolicy",
"iam:GetPolicy",
"iam:CreatePolicyVersion",
"iam:DeletePolicyVersion",
"iam:GetPolicyVersion",
"iam:ListPolicyVersions",
"iam:SetDefaultPolicyVersion",
"iam:CreateRole",
"iam:DeleteRole",
"iam:GetRole",
"iam:PassRole",
"iam:UpdateAssumeRolePolicy",
"iam:UpdateRole",
"iam:UpdateRoleDescription",
"iam:AttachRolePolicy",
"iam:DeleteRolePolicy",
"iam:DetachRolePolicy",
"iam:GetRolePolicy",
"iam:ListAttachedRolePolicies",
"iam:ListRolePolicies",
"iam:PutRolePolicy",
"lambda:ListTags",
"lambda:TagResource",
"lambda:UntagResource",
"lambda:AddPermission",
"lambda:GetPolicy",
"lambda:RemovePermission",
"lambda:ListVersionsByFunction",
"lambda:PublishVersion",
"lambda:CreateFunction",
"lambda:DeleteFunction",
"lambda:GetFunction",
"lambda:InvokeAsync",
"lambda:InvokeFunction",
"lambda:GetFunctionConfiguration",
"lambda:UpdateFunctionCode",
"lambda:UpdateFunctionConfiguration",
"lambda:DeleteFunctionEventInvokeConfig",
"lambda:GetFunctionEventInvokeConfig",
"lambda:ListFunctionEventInvokeConfigs",
"lambda:PutFunctionEventInvokeConfig",
"lambda:UpdateFunctionEventInvokeConfig",
"lambda:DeleteFunctionConcurrency",
"lambda:GetFunctionConcurrency",
"lambda:PutFunctionConcurrency",
"lambda:CreateEventSourceMapping",
"lambda:DeleteEventSourceMapping",
"lambda:GetEventSourceMapping",
"lambda:ListEventSourceMappings",
"lambda:UpdateEventSourceMapping",
"lambda:CreateAlias",
"lambda:DeleteAlias",
"lambda:GetAlias",
"lambda:ListAliases",
"lambda:UpdateAlias",
"logs:ListTagsForResource",
"logs:ListTagsLogGroup",
"logs:TagLogGroup",
"logs:TagResource",
"logs:UntagLogGroup",
"logs:UntagResource",
"logs:CreateLogGroup",
"logs:DeleteLogGroup",
"logs:DescribeLogGroups",
"logs:CreateLogStream",
"logs:DeleteLogStream",
"logs:DescribeLogStreams",
"logs:PutLogEvents",
"logs:DeleteResourcePolicy",
"logs:DescribeResourcePolicies",
"logs:PutResourcePolicy",
"logs:DeleteRetentionPolicy",
"logs:PutRetentionPolicy",
"s3:GetBucketTagging",
"s3:PutBucketTagging",
"s3:ListTagsForResource",
"s3:TagResource",
"s3:UntagResource",
"s3:CreateBucket",
"s3:DeleteBucket",
"s3:GetBucketPolicy",
"s3:PutBucketPolicy",
"s3:DeleteBucketPolicy",
"s3:GetBucketPolicyStatus",
"s3:GetBucketPublicAccessBlock",
"s3:PutBucketPublicAccessBlock",
"s3:GetBucketVersioning",
"s3:PutBucketVersioning",
"s3:GetEncryptionConfiguration",
"s3:PutEncryptionConfiguration",
"s3:GetLifecycleConfiguration",
"s3:PutLifecycleConfiguration"
],
"Resource": "*"
}
]
}
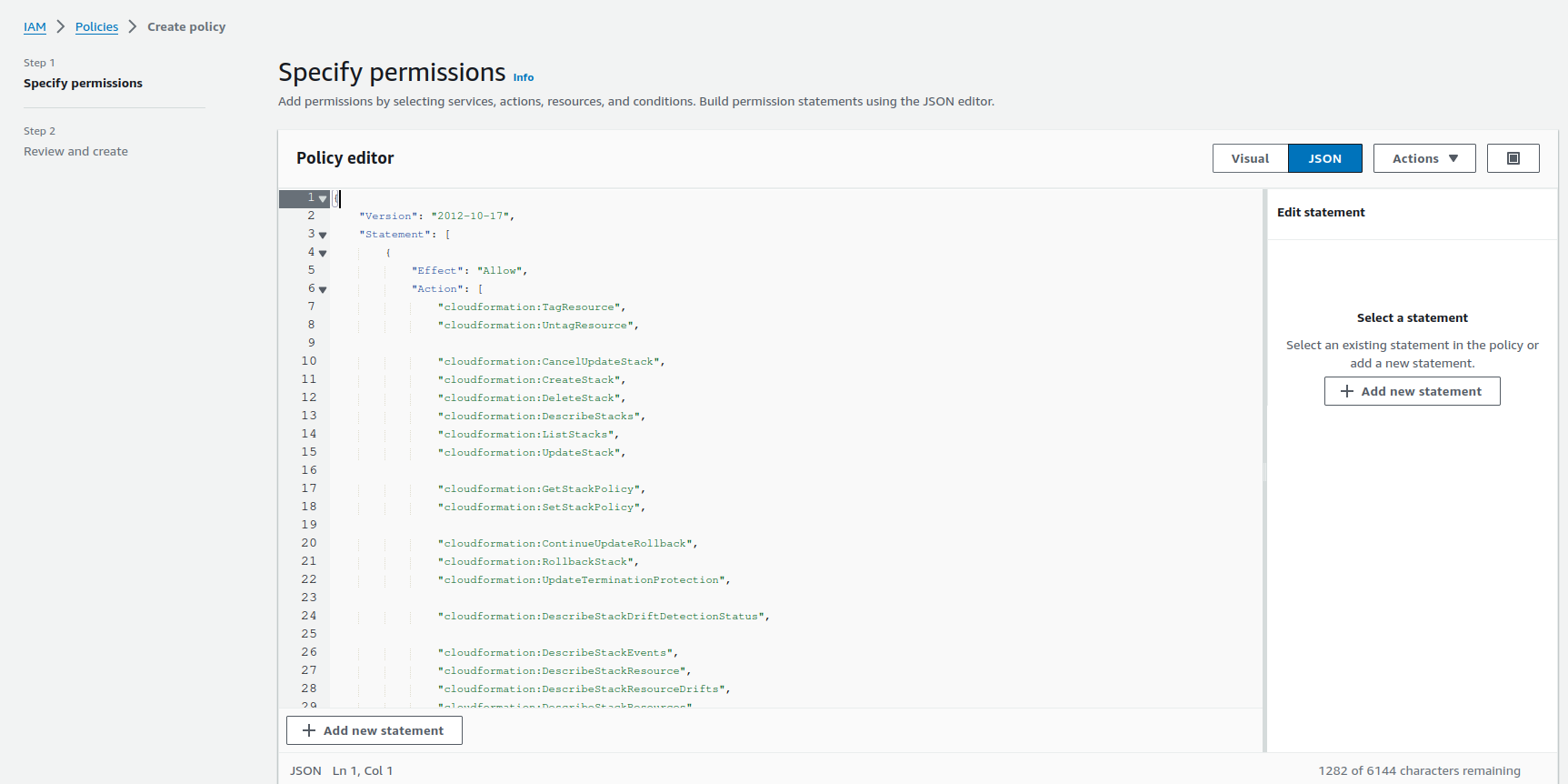
Figure 3: Create policy
- Press “Next”.
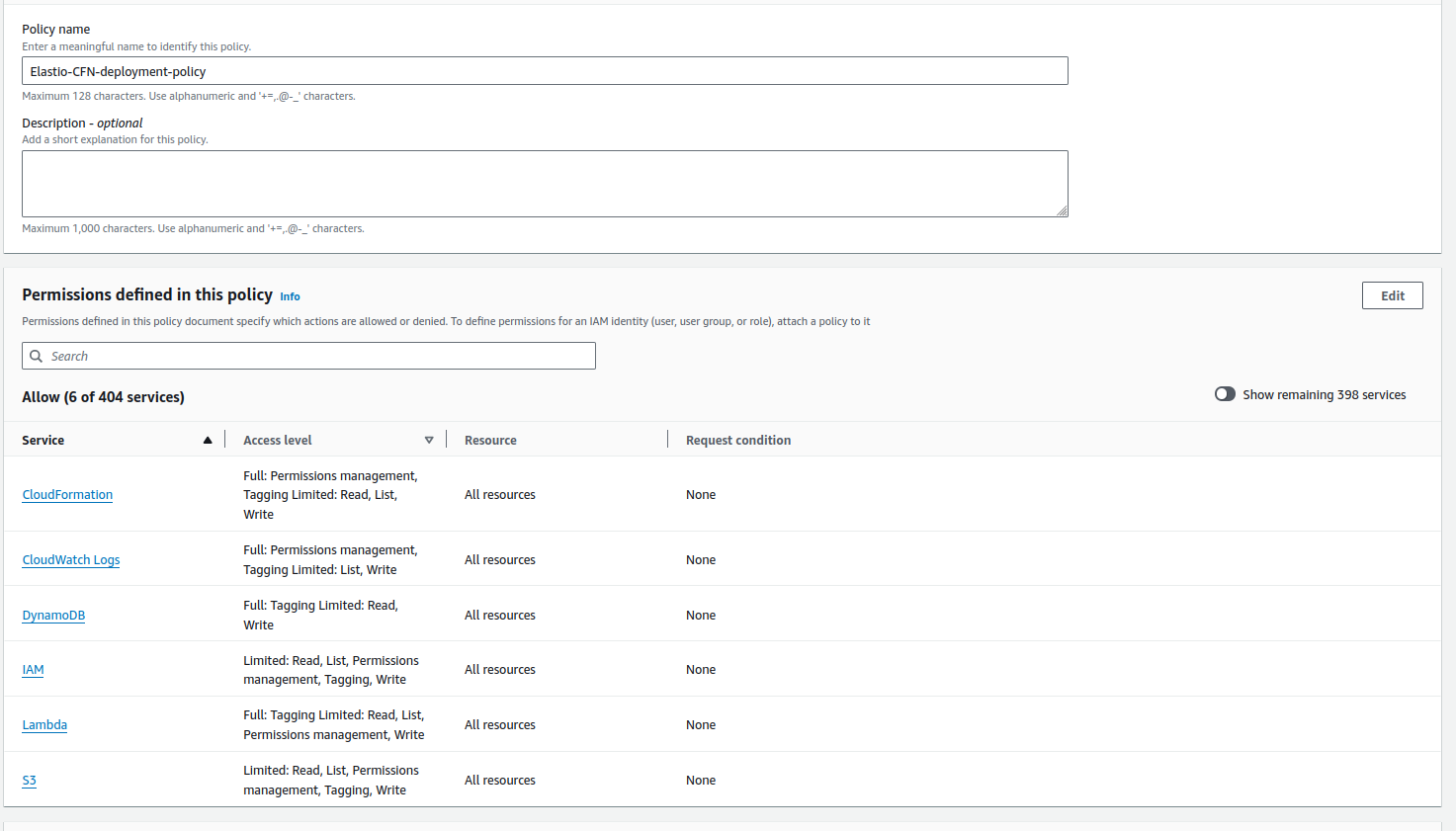
Figure 4: Review policy
-
Review the policy details and press the “Create policy” button. Go back to User creation flow. Press the update button on the policies list.
-
Start typing the newly created policy name. It will appear in the list, select the Elastio CFN deployment police and press “Next”.
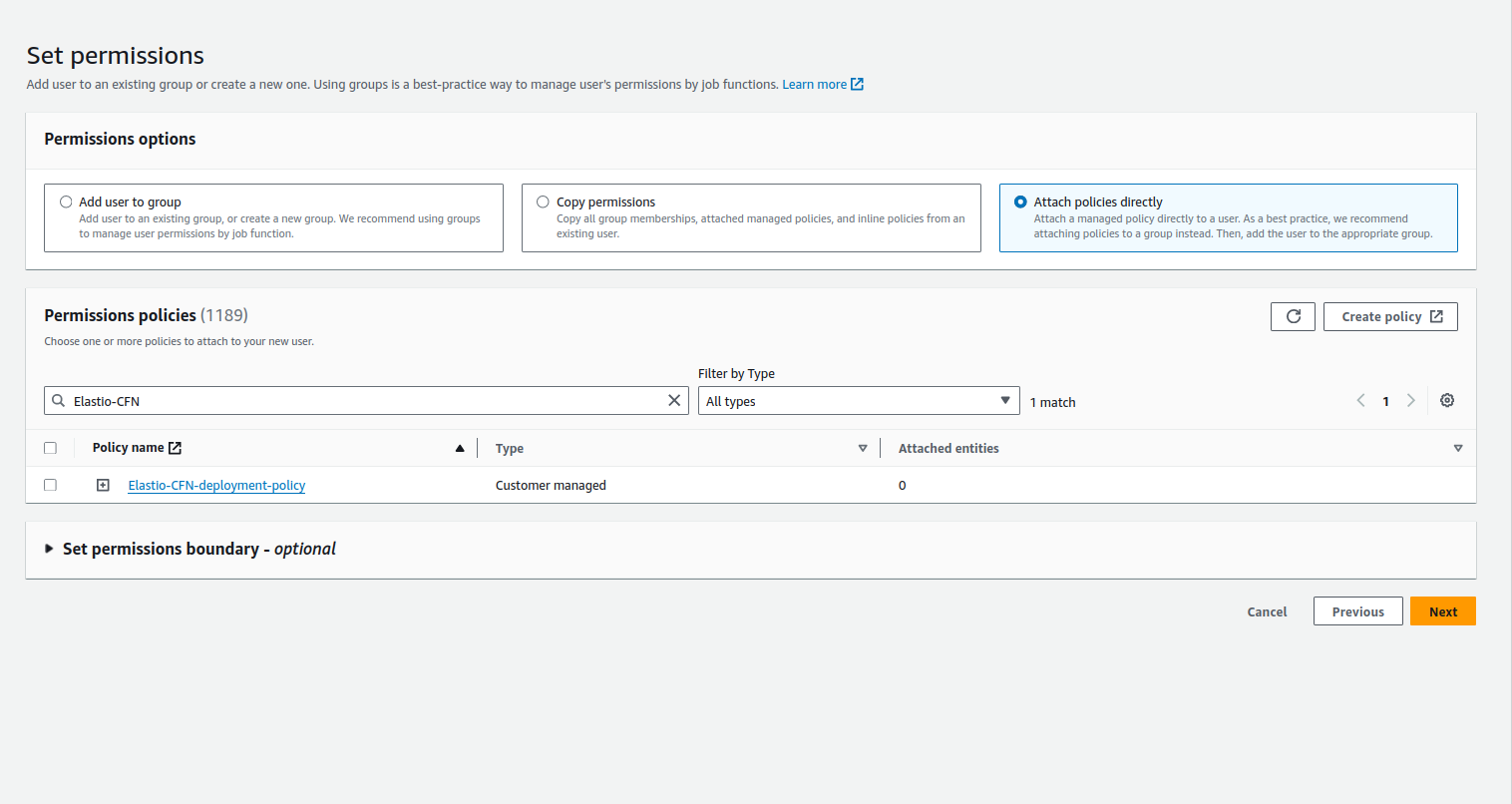
Figure 5: Select CFN deployment policy
- Review the user details and press the “Create user” button.
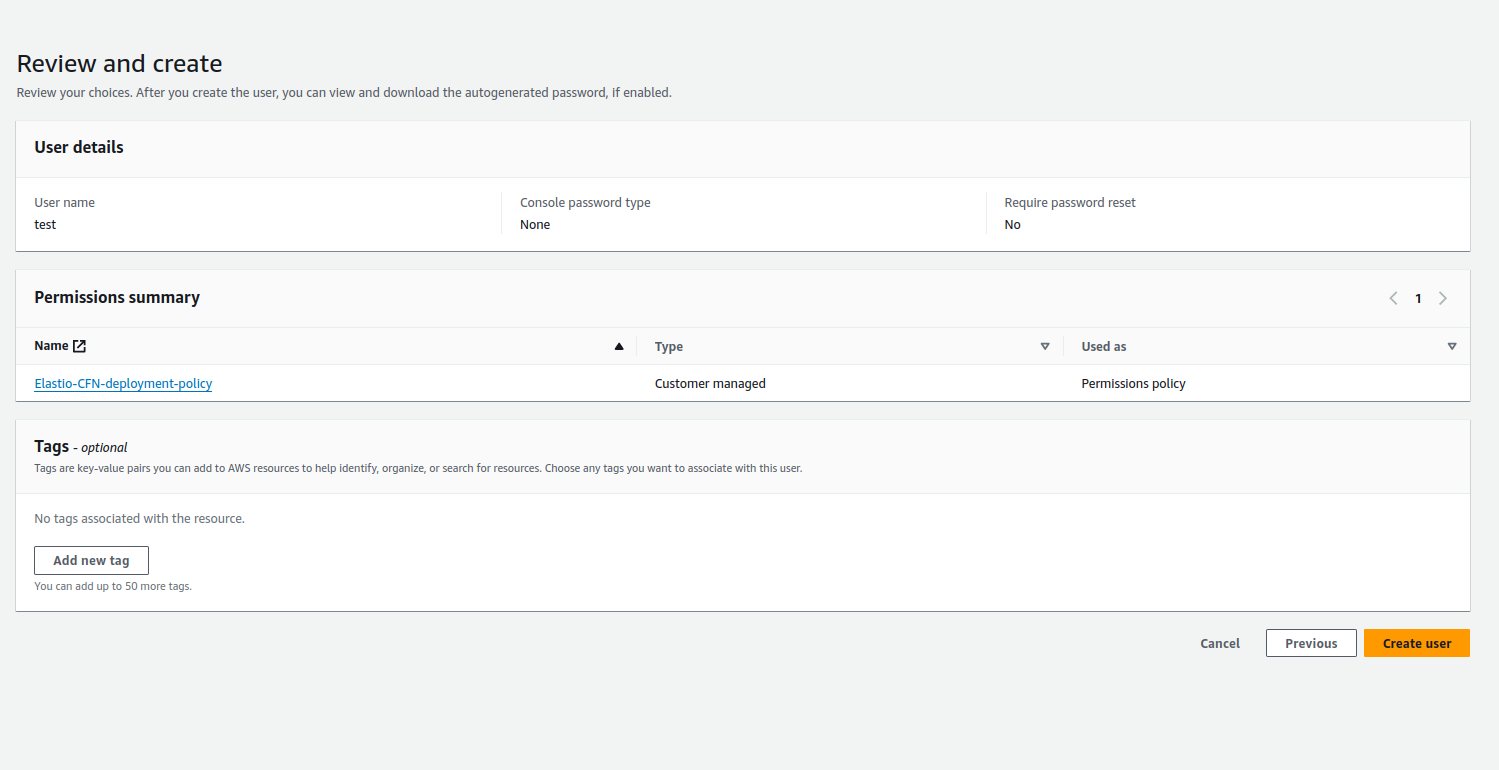
Figure 6: Create user
- A “Success” notification will be displayed.
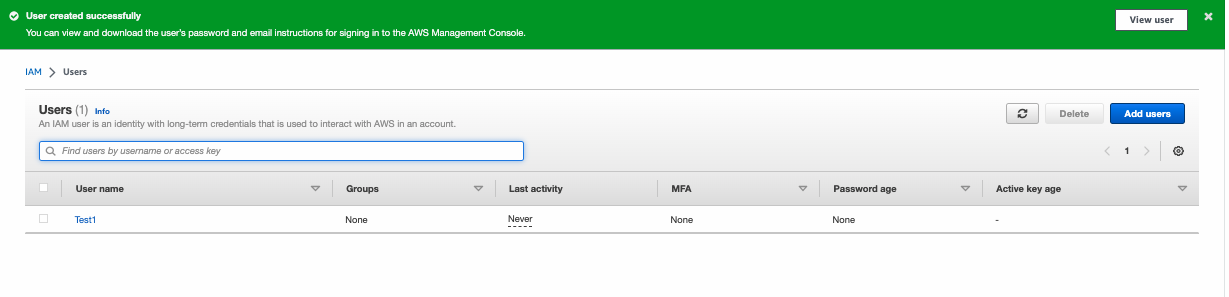
Figure 7: Success notification
Note: The added user is required for the CFN deployment and updates only and can be deleted after the completion of the process.